London Hosts Staged Cyberwar Exercises →
News, of the fifth edition of the Masterclass, a UK cyberwarfare exercise, held on board the HMS Belfast (one of the United Kingdom's five Imperial War Museums, and of course, in this case a former ship of the line, anchored on the Thames) comes to us by way of Ars Technica independent writer Emiko Jozuka.
"The competition, known as the Masterclass and developed by a group of cyber experts led by BT, is now in its fifth year and aims to plug the skills shortage currently affecting both governments and UK businesses. The competition essentially invites participants to put their skills to the test and experience a dramatized version of events faced by regular cybercrime fighting professionals. It also allows sponsors of the competition such as BT, Lockheed Martin, and Airbus, to hover on the sidelines and cherry pick the next cybercrime busting whizz kids." - Ars Technica's Emiko Jozuka
Ladar's Next Big Thing →
Old, still relevant, and the reasons' why... Wouldn't you say?
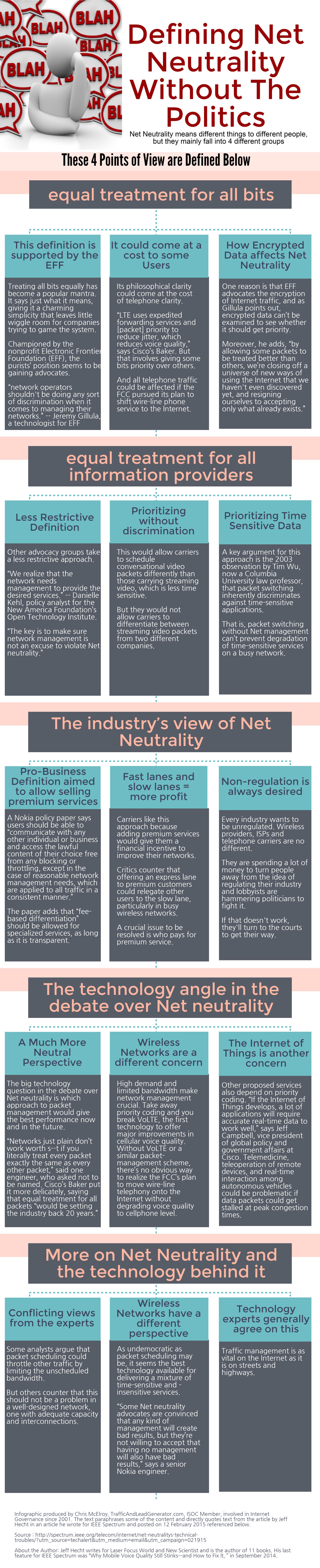
FCC Issues Net Neutrality Order Document →
The Federal Communications Commission has issued the codified order targeting Net Neutrality. Entitled FCC 15-24*, for GN Docket Number 14-28, In the Matter of Protecting and Promoting the Open Internet, Report and Order on Remand, Declaratory Ruling, and Order. At over *Four hundred pages long*, this document will (likely) become one of the most highly contentious Orders emerging this year (or the weapon of choice for conspiracy theorists due to it's weight*) from the Commission.
NIST Announces New Internal Report Targeting Smart Metering →
The National Institute of Standards and Technology (NIST) has announced a new internal report detailing a framework targeting Smart Meter Upgradability (NIST Internal Report NISTIR 7823), Advanced Metering Infrastructure Smart Meter Upgradeability Test Framework). Authored by Michaela Iorga (a member of the Computer Security Division, in the Information Technology Laboratory (ITL) at NIST) and Scott Shorter (of Electrosoft Services, Inc. in Reston, Virgina), the document is also available at the International DOI System under NIST.IR.7823.
I reckon the document's abstract sums it up quite nicely:
"As electric utilities turn to Advanced Metering Infrastructures (AMIs) to promote the development and deployment of the Smart Grid, one aspect that can benefit from standardization is the upgradeability of Smart Meters. The National Electrical Manufacturers Association (NEMA) standard SG-AMI 1-2009, “Requirements for Smart Meter Upgradeability,” describes functional and security requirements for the secure upgrade—both local and remote—of Smart Meters. This report describes conformance test requirements that may be used voluntarily by testers and/or test laboratories to determine whether Smart Meters and Upgrade Management Systems conform to the requirements of NEMA SG-AMI 1-2009. For each relevant requirement in NEMA SG-AMI 1-2009, the document identifies the information to be provided by the vendor to facilitate testing, and the high-level test procedures to be conducted by the tester/laboratory to determine conformance." - via NIST IR 7823
Meanwhile, you can also track, examine and attempt to contain your surprise at the latest, recognized industiral control systems & supervisory control and data acquisition systems vulnerabilities from our colleagues st US-CERT, here.
IARPA's Psychic Computational Device
Astonishing news, via NextGov's Aliya Sternstein of a purported Watson-like automated, IARPA supported psychic, computational device. Seemingly mythic in nature, this project has overtones of Forbin coupled with Verne... Operating under the moniker "Cyber-attack Automated Unconventional Sensor Environment", this is certainly a component of national security that bears additional scrutiny, eh Watson?
"IBM has even expressed interest in the "Cyber-attack Automated Unconventional Sensor Environment," or CAUSE, project. Big Blue officials presented a basic approach at a Jan. 21 proposers' day. CAUSE is the brainchild of the Office for Anticipating Surprise under the director of national intelligence. A “Broad Agency Agreement” -- competition terms and conditions -- is expected to be issued any day now, contest hopefuls say." - via NextGov's Aliya Sternstein
Syber-This, Syber-That
via the Wall Street Journal's inimitable Danny Yadron and Jennifer Valentino-DeVries comes the stupendous tale of too much Cyber in ones diet...
FAA Systems Found Vulnerable to Attack, GAO Reports
News, via The Washington Post's Ashley Halsey III of significant information security issues at the Federal Aviation Agency. In this case, the Government Accountability Office has published a new report entitled "FAA Needs to Address Weaknesses in Air Traffic Control Systems", detailing significant shortcomings in the agency's capability to fend off electronic attacks.
The GAO report facts speak volumes: The FAA has failed to fully implement the planned, 'agency-wide' information security program. The failure to implement and deploy is a tell-tale of questionable competency within the Agency's information security management, whose duty and primary task is protecting the National Airspace System (aka NAS), of which, should be the core competency of the FAA.
Time for a change at the FAA? Probably, however, the issue of foot-dragging is deeply systemic at the Agency, witness the multi-year effort to implement the FAA's Next Generation Air Transportation System (aka NextGen). Any change will most likely be accomplished over decades, rather than single digit years... After all, thirteen years post-FISMA and the Agency has not yet implemented and deployed the mandated FISMA requirements, is, in a word - astonishing.
Now, focusing on the issues, we turn to the GAO discovered chllanges the FAA faces (of which, a statement from the GAO appears below, and is a direct excerpt from the published report. Read it, my fellow citizens, and weep.
"While the Federal Aviation Administration (FAA) has taken steps to protect its air traffic control systems from cyber-based and other threats, significant security control weaknesses remain, threatening the agency's ability to ensure the safe and uninterrupted operation of the national airspace system (NAS). These include weaknesses in controls intended to prevent, limit, and detect unauthorized access to computer resources, such as controls for protecting system boundaries, identifying and authenticating users, authorizing users to access systems, encrypting sensitive data, and auditing and monitoring activity on FAA's systems. Additionally, shortcomings in boundary protection controls between less-secure systems and the operational NAS environment increase the risk from these weaknesses.
FAA also did not fully implement its agency-wide information security program. As required by the Federal Information Security Management Act of 2002, federal agencies should implement a security program that provides a framework for implementing controls at the agency. However, FAA's implementation of its security program was incomplete. For example, it did not always sufficiently test security controls to determine that they were operating as intended; resolve identified security weaknesses in a timely fashion; or complete or adequately test plans for restoring system operations in the event of a disruption or disaster. Additionally, the group responsible for incident detection and response for NAS systems did not have sufficient access to security logs or network sensors on the operational network, limiting FAA's ability to detect and respond to security incidents affecting its mission-critical systems.
The weaknesses in FAA's security controls and implementation of its security program existed, in part, because FAA had not fully established an integrated, organization-wide approach to managing information security risk that is aligned with its mission. National Institute of Standards and Technology guidance calls for agencies to establish and implement a security governance structure, an executive-level risk management function, and a risk management strategy in order to manage risk to their systems and information. FAA has established a Cyber Security Steering Committee to provide an agency-wide risk management function. However, it has not fully established the governance structure and practices to ensure that its information security decisions are aligned with its mission. For example, it has not (1) clearly established roles and responsibilities for information security for the NAS or (2) updated its information security strategic plan to reflect significant changes in the NAS environment, such as increased reliance on computer networks.
Until FAA effectively implements security controls, establishes stronger agency-wide information security risk management processes, fully implements its NAS information security program, and ensures that remedial actions are addressed in a timely manner, the weaknesses GAO identified are likely to continue, placing the safe and uninterrupted operation of the nation's air traffic control system at increased and unnecessary risk." via the United States Government Accountablity Office Report "FAA Needs to Address Weaknesses in Air Traffic Control Systems"
Gatekeeper
via MacObserver's John F. Braun, comes this chilling tale of a fundamental flaw in Apple Inc.'s MAC OS X Gatekeeper, and how to apply apropos bandaidery, as it were...
Google Creates Quantum Chip →
News, via Wired's Robert McMillan, of trouble in paradise. In this case, an error prone computational quantum platform the search leviathan Google Inc. (NasdqGS: GOOG) is running, down yonder in Mountain View...
"The crux of the problem is a phenomenon called bit-flipping. This happens when some kind of interference—cosmic rays, for example—causes the bits stored in memory to “switch state”—to jump from a 0 to a 1 or vice versa. On a PC or a server, error correction is relatively easy." - via Wired's Robert McMillan
- Image depicts a D-WAVE branded quantum computational device
Bad Decisions At Oracle
Meanwhile, in idiotic-decisions-made-by-a-Fortune-500-Company news... Quite likely one of the world's largest software publishers - Oracle Corporation (NYSE: ORCL) has been installing adware along with the JAVA SE Runtime and other JAVA applications on user machines. Evidence of Greed or just Bad Decisions, you be the judge. In this case, when installing the JAVA bits, the ASK.com toolbar is loaded onto the unfortunate victims machine (users can opt-out, but it is not an easy choice to make).
"Tests on a Mac running the latest OS X release proved Oracle's newest Java installer will tack on the Ask extension to both Google's Chrome browser and Apple's Safari, using what some may consider deceptive practices. The option to install Ask is selected by default, meaning users proceeding through installer pop-ups are unlikely to notice the adware until they open a new browser window. Once installed, Ask's extension points the browser's homepage to Ask.com and inserts the Ask toolbar just below the address bar." - via AppleInsider