Data Melt →
Evidence, says Zack Whittaker for Zero Day, of data disappearing from solid-state storage facilities, when the storage medium is unpowered for several days. Apparently, additional degradation takes place when temperatures rise...
The money quote:
"A recent presentation by hard drive maker Seagate's Alvin Cox warned that the period of time data is retained on some solid-state drives is halved for every 9°F (or 5°C) rise in temperature where its stored. That means if a solid-state drive is stored in a warm room, say 77°F (25°C), its data can last for about two years. But, if that goes up by a mere few degrees to 86°F (30°C), that data's retention period will be cut in half." via Zack Whittaker at Zero Day
GRR Find All the Badness, Collect All the Things →
Google Inc.'s {NasdaqGS: GOOG) GRR Rapid Response, an incident response framework focused on remote live forensics.
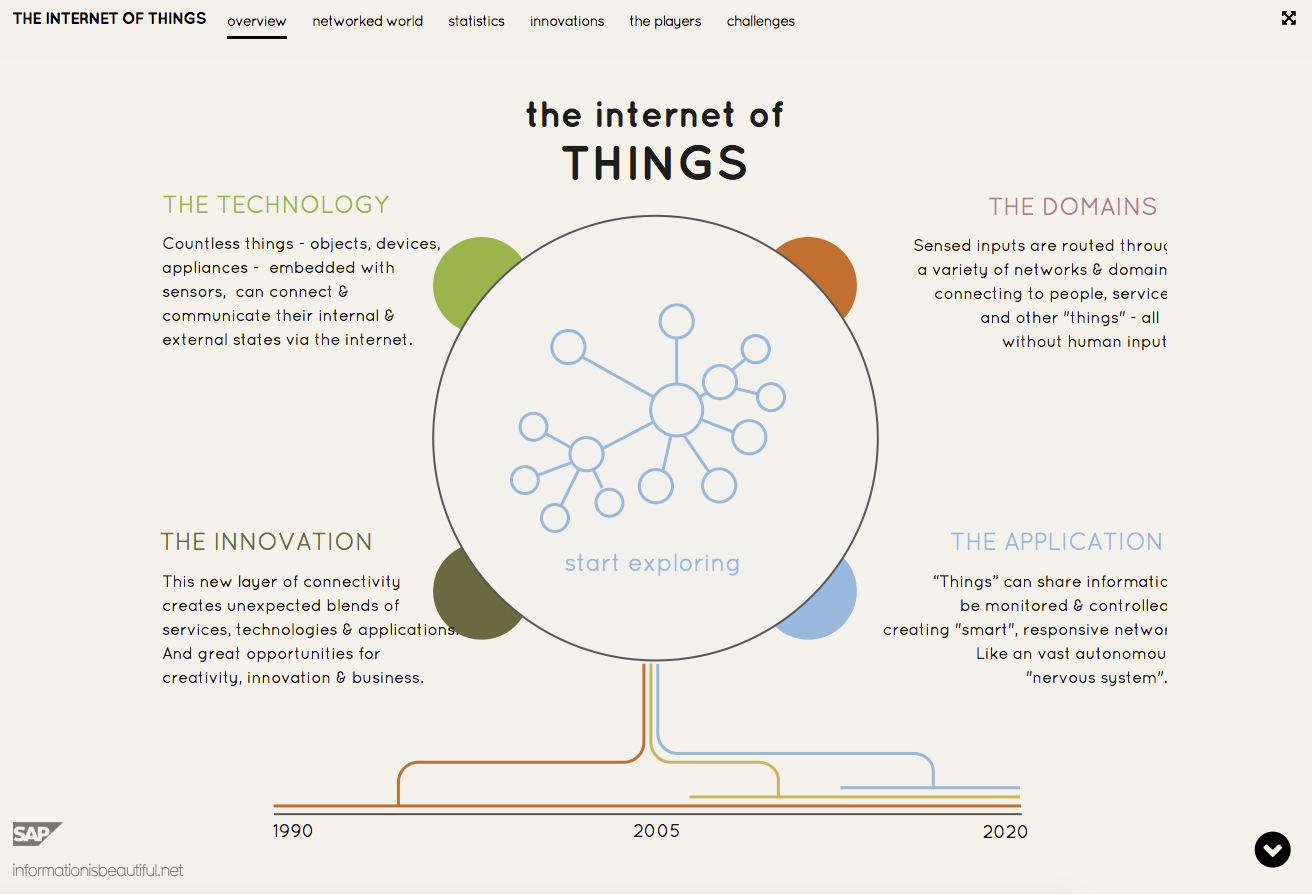
Information is Beautiful: IoT
via Information is Beautiful, comes this superlative interactive infographic, detailing what you need to know about the Internet of Things.
DARPA and BBN, 'A History of the ARPANET: The First Decade' →
Bolt Beranek and Newman (BBN) Report #4799 Document entitled 'A History of the ARPANET: The First Decade'. First published in 1981, and detailing early ARPANET engineering, via the March 2015 'The Internet Protocol Journal' (Volume 18, Number 1). Download IPJ back issues and find subscription information at Internet Prorocol Journal.
FCC Denies Delay Requests, Net Neutrality Rules On The March →
via Grant Gross, writing at PC World, comes news of the United States Federal Communications Commission denial of submitted requests from a group of Cable and Telephony providers (the ususal suspects) to slow the implementation of the Commission's Net Neutrality rules. This, my fiends, is one commish we can all get behind (except, of course, the Cable, Telephony and their lobbyists).
CyberLock Versus IOActive, Targets Lock Research As DMCA Violation →
Reports of threats made by attorneys for CyberLock targeting security researchers at IOActive have appeared at Ars Technica. The piece, written by the inimitable Dan Goodin, details the work accomplished by the researchers. We've seen this form of bad behavior by outed lock manufacturers before, interestingly - most (if not all) to no avail.
The money quote:
'Thursday's advisory from security firm IOActive is notable not only for the serious security issues it reported in the CyberLock line of access control systems, which are certified to meet a wide range of US governmental requirements and certifications. The report is also the topic of a legal threat from CyberLock attorneys who invoked draconian provisions of the Digital Millennium Copyright Act if IOActive disclosed the vulnerabilities. A redacted version of a letter CyberLock outside attorneys sent IOActive researcher Mike Davis has reignited a long-standing tension between whether it should be legally permissible for researchers to publicly disclose unfixed vulnerabilities in the products they test.' - via Dan Goodin at ArsTechnica
Harbortouch'ed →
via the inimitable Brian Krebs, writing at Krebs On Security, comes the latest sorry tale of attacked, and successfully breached, Point of Sale (POS) terminals manufactured by POS system purveyor Harbortouch.
NetFlix Unleashed FIDO →
via Netflix's Jason Chan, comes word of a OSS automation effort targeting security related events, and actions thereo. Monikered FIDO or more accurately 'Fully Integrated Defense Operation' the system ostensibly serves as an orchestration layer for automated response activities, in the case of security event triggers. Comprised of a well thought-out architecture of infrastructure components, an encapsulated orchestration, correlation and scoring engine coupled to a threat intelligence system... But, I'll leave the full explanation in the obviously capable hands of Netflix's Security Team; examine. if you will, FIDO at GitHub. And, because it's Open Source Software, the security community at large can reap the benefits of this superalitve effort. Outstanding.
Mumblehard, The Pernicious →
Swati Khandelwal, writing at The Hacker News, regales us with the tale of Mumblehard, the Linux and BSD Server targeted attack malware that transforms those machines into pernicious spambots.
NIST CSD, ITL, CPP Slated to Host 8th Cloud Computing Forum →
NIST's Computer Security Division and the Information Technology Laboratory (ITL) along with the NIST Cloud Computing Program has announced hosting of the 8th Cloud Computing Forum and Workshop. Registration Information, etc. can be viewed here. Included with the announcement is the Call for Abstracts, noted below:
- Abstract Submission Deadline: May 15, 2015
- Abstracts Review Deadline: June 1, 2015
- Presentation Submission Deadline: July 1, 2015
Interested? Download the 8th Cloud Computing Forum and Workshop Abstract Submission form, additional information resides here.
Kalle Ljung's Astounding Antarctica
Occasionally, a motion picture makes itself known hereabouts, with absolutely extraordinary visage of a land previously unsullied. This is such a picture. Enjoy!
Sparks' End of Show Report →
Estonia, Creates Volunteer Cyberwarrior Brigade
Considering the country's highly systems-literate populis, this is one of the more interesting cases of a so-called Cybernational Guard, this time, stationed at the K5 Barracks (NATO Cyber Defense Center, Tallinn, Estonia), in quite likely one of the most astoundingly beautiful countries on our planet - Estonia!