Google Employees Ironic Chinese Protest
Whilst Google Employees Protest Chinese Market Google Rentry Products, They Have No Problem With Other Users... Where's the Indignation About Privacy Invading Google Behaviors In The US, Canada, Méxicó and elsewhere? Just shameful.
Larry Seltzer's 'Data encryption: How To Avoid Common Workarounds'
via the inimitable Larry Seltzer, comes this superlative post over at HPE; in which, Mr. Seltzer details data encryption workarounds, and a method to avoid same. Definately, today's Must Read.
Facebookery: Huawei, Other Chinese Manufacturers Slurp Facebook Data →
via Ina Fried and David McCabe, writing at Axios, comes the latest revelation of feckless user data management at Facebook Inc. (Nasdaq: FB); this time, the event comes with smarmily justified sharing of Facebook Inc. user data (without user consent) to Chinese manufacturers' (including People's Republic of China's Peoples Liberation Army controlled Huawei and others) by Francisco Varela, Facebook, Inc. Vice President - Mobile Partnerships Varsela, also (apparently) is a shill ( here) for First Republic Bank. Enjoy today's Must Read and this! H/T
“Huawei is the third largest mobile manufacturer globally and its devices are used by people all around the world, including in the United States. Facebook along with many other U.S. tech companies have worked with them and other Chinese manufacturers to integrate their services onto these phones. Facebook's integrations with Huawei, Lenovo, OPPO and TCL were controlled from the get go — and we approved the Facebook experiences these companies built. Given the interest from Congress, we wanted to make clear that all the information from these integrations with Huawei was stored on the device, not on Huawei's servers.”' - Francisco Varela, Vice President - Mobile Partnerships, Facebook Inc.
Lurking: Another Credit Reporting Agency, Managed By Equifax!
via Brian Krebs, writing, investigating and generally-doing-the-right-thing at Krebs on Security, details the emergence of another credit reporting entity managed by the aggregated incompetents at Equifax. Monikered 'National Consumer Telecommunications and Utilities Exchange' Astounding.
Blatant & Pervasive Incompetencies, Recent History of →
Recalling other crisis management fails - in the wake of Facebook's stunning (and probably feigned) ignorance of data exfiltration on their own platform: Via the obviously talented Michael Grothaus, whilst writing at Fast Company, comes this interesting recent history of crisis management at companies-of-note. You will - I am certain - notice a recurring theme of fathomless lack of intellectual capacity. Today's Must Read and filed under 'Blatant Stupidity'. Enjoy!
SQL Security Chronicles →
Quite likely, the single most significant data security educational series of blog posts this year - via the Imperva Cyber Security Blog,written by Elad Erez and Luda Lazar - now in Part 3 of the series (Part 1 and Part 2 are highly recommended as well). Rather than put my spin on what Elad and Luda have presented on the Imperva blog, I'll let their brilliant speak tell the tale! Today's highly important Must Reads.
India's AADHAAR: The Troy Hunt Security Analysis →
In typically excellent form, Troy Hunt analyzes ostensibly the largest biometric data system in the world, comprising at least 1.2 billion records of bio-data markers. Absolutely phenomenal and, Today's Must Read.
AWS CloudFront Field Data Encryption, Protection for the Rest of Us →
Superlative AWS blog post by Alex Tomic and Cameron Worrell, detailing some of the best news yet in encryption capability on Amazon Web Services - table contained field level encrytion. With prudent end-to-end cryptographically protected data objects, I cannot emphasize how important it is to make this form of data-at-rest encryption available to your Security Architects, DBAs, Developers and Security Engineers as part of that end-to-end solution. Outstanding.
"Field-level encryption addresses this problem by ensuring sensitive data is encrypted at CloudFront edge locations. Sensitive data fields in HTTPS form POSTs are automatically encrypted with a user-provided public RSA key. After the data is encrypted, other systems in your architecture see only ciphertext. If this ciphertext unintentionally becomes externally available, the data is cryptographically protected and only designated systems with access to the private RSA key can decrypt the sensitive data." - AWS Blog Posting by Alex Tomic and Cameron Worrell
Seth Juarez's 'An Introduction to Blockchain with Mark Russinovich' →
Very well crafted, well presented and on target video, comprising blockchain content from Seth Juarez and Mark Russinovich. Deemed today's Must View video. Enjoy (and consider having your parents, grandparents and most of all your kids watch as well).
Macie the Discoverer →
News that Macie The Discoverer has arrived in your S3 bucket... Data Security Automation - potentially - at it's finest? You be the judge.
The Disingenuous →
Do you unequivocally trust iRobot with your personal data, including internal mapping of your home? Read this post to learn more.
NKOTBlockchain →
Eh, wot? New Kids on the Blockchain? No - simply put, it's the proliferation of Blockhain technology (in this case distributed database schema) into industrial processes. via the UK's The Engineer, and writer Andrew Wade, comes the news of said blockhain spread. Today's MustRead!
Meet Alice and Bob →
Clouding Up →
via Gizmodo investigative reporter Dell Cameron, comes the astounding news of the systemic incompetence in properly handling secret documents and other artifiacts stored within the cloud (in this case, AWS S3 Buckets) by a well established contractor to the National Geospatial-Intelligence Agency (NGA). Certainly, a first-rate example of an Expanding Cloud of Lethal Stupidity (ECOLS).
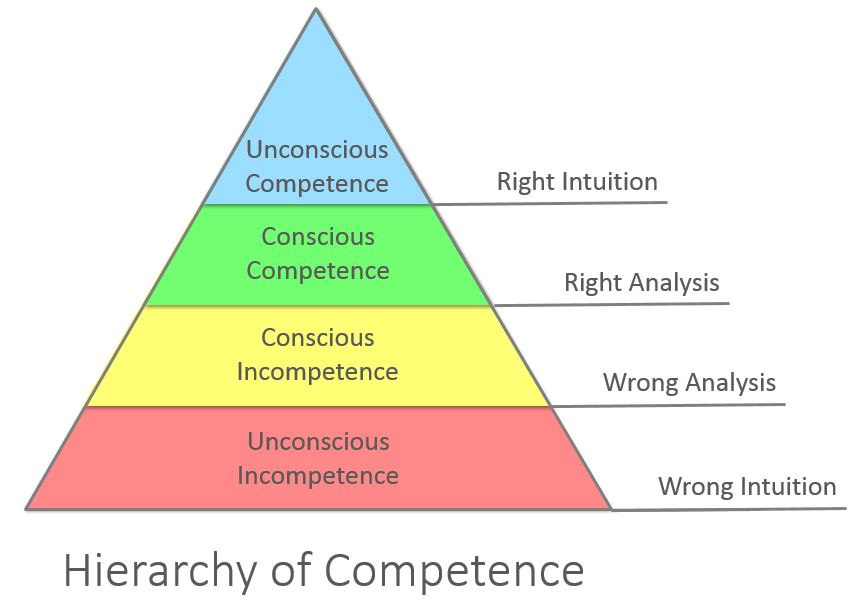
Where does the organization in question fall within the Noel Burch Hierarchy of Competence model?. Should the culprits in this scenario be prosecuted? You be the judge. Truly astounding, indeed.
"A cache of more than 60,000 files was discovered last week on a publicly accessible Amazon server, including passwords to a US government system containing sensitive information, and the security credentials of a lead senior engineer at Booz Allen Hamilton, one of the nation’s top intelligence and defense contractors. What’s more, the roughly 28GB of data contained at least a half dozen unencrypted passwords belonging to government contractors with Top Secret Facility Clearance." - via Gizmodo reporter Dell Cameron
Suit of Bose →
News of an interesting privacy related lawsuit, via Fortune writer Jeff John Roberts, is now swirling around personal electronics manufacturer Bose Corporation. Apparently, collecting data (and a viloation of the so-called Wire Tap Act (Codified in 18 U.S.C. §§ 2510-2522)) - through a companion app to the company's best-in-class noise canceling headphones, and the misuse thereof, is the gist... Stay Tuned. Hat Tip
"The complaint accuses Boston-based Bose of violating the WireTap Act and a variety of state privacy laws, adding that a person's audio history can include a window into a person's life and views. "Indeed, one’s personal audio selections – including music, radio broadcast, Podcast, and lecture choices – provide an incredible amount of insight into his or her personality, behavior, political views, and personal identity," says the complaint, noting a person's audio history may contain files like LGBT podcasts or Muslim call-to-prayer recordings." - via Fortune writer Jeff John Roberts
Goatse of Cloudbleed →
via the eponymous Phoneboy, comes his take on the latest security foible of a major backend provider (in this case Cloudflare), entitled 'Cloudflares with a Chance of Goatse', Mr. Welch-Abernathy explains it all, in imitiable form. Today's MustRead.
ACM CFP - CODASPY 2017 →
General Chair for the Organizing Committe of the ACM Conference on Data and Appilication Security and Privacy - Gail-Joon Ahn - has issued a Call for Participation for the Confab. Slated for March 22, 2017 through and inclusive of March 24, 2017. THis is sure to be an outstanding conference, with both two outstanding keynotes (which can be found here: http://www.codaspy.org/keynotes/.
Organizing Committee:
- General Chair: Gail-Joon Ahn, Arizona State University
- Program Co-Chairs: Gabriel Ghinita, University of Massachusetts at Boston, Alexander Pretschner, Technische Universität München
- Industry Track Chair: Elisa Bertino, Purdue University
- Poster Chair: Jaehong Park, University of Alabama in Huntsville
- Panel Chair: Adam Doupe, Arizona State University
- Proceedings Chairs: Martin Ochoa, Singapore University of Tech. and Design and Hongxin Hu, Clemson University
- Publicity and Web Chair: Ram Krishnan, UT San Antonio
- Workshop Chair: Adam Lee, University of Pittsburgh
- Local Chair: Ziming Zhao, Arizona State University
- Organization Chairs: Kristina Nelson, Arizona State University and
- Melissa Pagnozzi, Arizona State University
- Steering Committee: Ravi Sandhu, UT San Antonio (Co-Chair), Elisa Bertino, Purdue University (Co-Chair), Alexander Pretschner, Technische Universität München and Gail-Joon Ahn, Arizona State University